BI – For safety reasons
BI – Thoughts (5) – Cadran publishes a series of articles on the ideas surrounding Business Intelligence in combination with Oracle JD Edwards. In these articles various considerations and reflections are discussed, which can be helpful in making the right decisions in the implementation and application of both systems. The previous articles dealt with the star scheme, facts, dimensions and the interplay between these two. This article discusses the administrative organization, the control technical functional separation and the security that goes with it.
When Business Intelligence is deployed company-wide to unlock information within (or even outside) the organization, security can not be omitted. Users of the software can be divided into groups and / or departments and have certain roles by their functions. It is undeniable that certain data may or may not be visible.
BI Security
A user who logs into BI, therefore resides under one or more groups. Groups are linked to roles and those roles have privileges and permissions. Out of the box comes Oracle Business Intelligence with the following roles:
- BI Consumers – Can view BI Objects (Dashboards & Analytics) interactively.
- BI Authors – Are allowed to set up (ad hoc) Analytics and may store these in their personal work environment.
- BI Administrators – Can set up shared Dashboards and publish the (manufactured by Authors) Analytics.
The last role also has the rights to perform system administration, user maintenance and development work.
In practice, BI Consumers will be divided into functional roles in the organization, which will be restricted to what they can see. BI Administrators will usually be allowed to see and do everything. BI Authors are the intermediate form. Depending on the organization, they will be able to provide information needs for the entire organization and all subject areas and thus have access to all information or be restricted to a specific area on which they may report. Depending on the size and complexity of the organizational structure, several specific layers and combinations of rights can be applied here.
Privileges and Permits are on two important levels:
- Web Catalog – Who can view which BI Object (Dashboard pages & Analytics) and which function buttons are available?
- Common Enterprise Information Model – Who has access to which components from the information model and which data filtering plays?
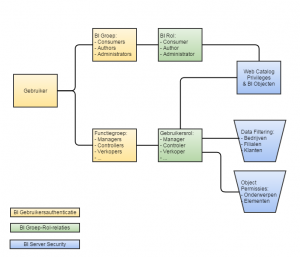
Schematically the above relates as follows:
With the following additional and explanatory comments:
- Rights are linked to roles;
- Roles are linked to groups;
- Users are linked to groups;
- It is recommended to keep groups and roles one on one, but mixing is possible. If conflicts arise (one role may be allowed, the other does not), then the approach of Most Restriction is applied;
- Web Catalog Privileges & BI Objects controls which dashboards someone sees and which applications can be executed;
- Data filtering refers to the curtailment of data that someone can view, such as only from their own company or branch offices or from their own customers;
- Object permissions refers to the data elements that are available, such as subject areas and columns within them. For example, it can be arranged that someone has access to the subject area Revenue and within that the Marge may or may not see.
It is always advisable to work with so-called negative security. This means that everyone can not do anything, unless explicitly granted access.
JD Edwards Security
When Oracle JD Edwards has been in use for some time, similar technical checks will be made to support the administrative organization. The Oracle BI technique allows us to use and apply the set-up (for example Row Security on Company or Business Unit) in the Common Enterprise Information Model and this seems obvious.
However: A JD Edwards user is generally an operational back-office employee. Oracle Business Intelligence users are at all levels of the organization on both operational, tactical and strategic levels. A director or a sales representative may make grateful use of the interactive dashboards, but not as quickly a user within Oracle JD Edwards.
In addition, of course, the consideration of licenses of these systems, but more importantly, that Oracle Business Intelligence may serve more subject areas than just the ERP administration. In addition to, for example, Accounts Receivable and Revenue analyzes, a Human Resource Management System and a Laboratory system can also be opened up.
A nice intermediate form can be found in the operational reporting component in Oracle BI, namely BI Publisher. In combination with Oracle JD Edwards, this reporting tool has a special possibility to access the data via the Oracle JD Edwards Data Access Driver (DAD). By accessing the data from JD Edwards via this connector, the data security of JD Edwards is applied. Because it is assumed that the user, who logs on this tool, also exists within JD Edwards, the row-security of JD Edwards can be applied and the user sees with BI Publisher reports the same data, which is also shown within JD Edwards. to become. An additional advantage of this connector is that it works not only through the row-security of JD Edwards, but also through the Data Dictionary of JD Edwards. As a result, descriptions of tables, columns and UDC codes are immediately available and dates and numbers are presented in the same format as in JD Edwards. The standard documentation from Oracle JD Edwards with BI Publisher provides extensive information here.
One Identity Store
Oracle is integrating all software more and more with the possibilities for a single Identity Store, in which all users of all systems are centrally registered. Authentication of users takes place against this one central system and thus they get the rights and accesses to the relevant applications at the right level. This can take the form of Oracle Single Sign On or via for example Microsoft Active Directory (the standard Windows logon).
Oracle JD Edwards knows the possibilities to authenticate users against such a central user bank. Oracle Business Intelligence actually even assumes this. The Web Logic Server on which the software runs has its own users, groups and roles, but assumes that an external application provides the users and groups. It is the trend that Oracle provides more and more applications with central authentication and security in this way and it is in line with the expectations that JD Edwards security will also be shaped in this way
In a later article, the way in which Oracle Business Intelligence can be provided by a so-called LDAP provider, with which users can be registered via Microsoft Active Directory.
Data Filtering
A powerful element of the possibilities within Oracle Business Intelligence is the data filtering. In the different subject areas, filters can be set up for the different roles, which limit data to what someone can see. An obvious example of this is Company Security. This means that a director can see information about all companies and a manager BeNeLux only information about a limited set of companies. This requires in the initial setup that somewhere which users or groups or roles have access to which companies. Oracle BI can use those relationships in the information model. The data filters are added in that information model and when a user views a certain dashboard, data (both facts and dimensions) will be restricted to only the permitted ones. It simply means that this restriction under water is added to the where clause of the query.
This offers an extremely versatile and flexible mechanism to limit the information for users to what they are entitled to, without having to change the BI Model and / or the dashboards in structure or to develop specific dashboards for specific functional areas.
Dashboards & BI Objects – The Web Catalog
A Dashboard in Oracle BI serves information about a specific subject area. A dashboard can consist of multiple pages and on dashboard pages there is Analytics. All these BI objects are stored in the Web Catalog, a directory structure with a logical structure. By setting up this structure conveniently, it is then possible to give the right roles access to the right dashboard pages and parts from that Web Catalog. In this way it can be prevented that a HR personnel also gets to see the dashboard with Sales Information. The management tools of Oracle BI offer a versatile and powerful maintenance mechanism for achieving a high degree of flexibility and ease of use.
Pars Pro Toto
An example:
A branch manager has insight into the revenue figures of his own store in Oracle BI. In addition, Oracle BI shows him what share his store contributes to the total Revenue and how well it does compared to other stores. However, he has no insight into the information of the other stores.
The above example seems security-technical an impossibility and paradox. However, Oracle Business Intelligence has the tools to make the above possible. This can even go so far that this so-called Pars Pro Toto (or part of the whole) is only shown if this figure is composed of, for example, more than five components. After all, if only two stores are involved in the total, it is very easy for the branch manager to deduce which part the other store provides. In this way it can also be served that averages and contributions are only displayed when they form a representative sample of the data. For example, it can be arranged that a certain percentage only appears if the average consists of at least 10 elements.
This is an example of the powerful analysis capabilities that the Oracle Business Intelligence toolset offers.
Definities – One Version of the Truth
Once again, everything stands or falls with definitions. After all, data filtering restricts what you see and thus influences the complete truth. It is therefore important to include the roles, groups and data filtering in the description of the company definitions in the aforementioned company dictionary. Turnover is not just Turnover. The content of the grade depends on:
- How this is defined in terms of operating technology
- Which implementation issues in Oracle JD Edwards have been applied to administer this
- What conditions underlie the presentation
- Which restrictions must be applied from a security point of view
It is therefore important to involve security at an early stage in the analysis and design of the applications in Oracle Business Intelligence. It can have a major influence on the choices and approach of the realization and thus on the truth that one sees.
Security Matrix
The whole structure and structure of roles, groups and rights can best be captured in a so-called Security Matrix. It is possible to record which data and objects belong in Oracle Business Intelligence. In this way one keeps insight in this structure and that guarantees the manageability. Application and System administrators will have to think about which roles and groups have access to this form when new subject areas and new dashboards are delivered in BI. The tools literally offer only the tools. The business processes dictate the substantive aspects.
A later article discusses the Act-As functionality of Oracle Business Intelligence. A mechanism that can be a very good tool when testing and replaying the security setup.
The implementation of a BI solution is more than the implementation of a software solution. Cadran’s vision is focused on determining the right information that is available to the right people in your organization at the right time. A thorough project approach is very important to prevent the pitfalls of such an implementation. BI is not about developing reports or creating nice dashboards. BI is about managing your organization and Cadran is your partner when it comes to Business Intelligence and JD Edwards. Do you want to know more?
Author: Rick Brobbel
BI Consultant at Cadran Consultancy